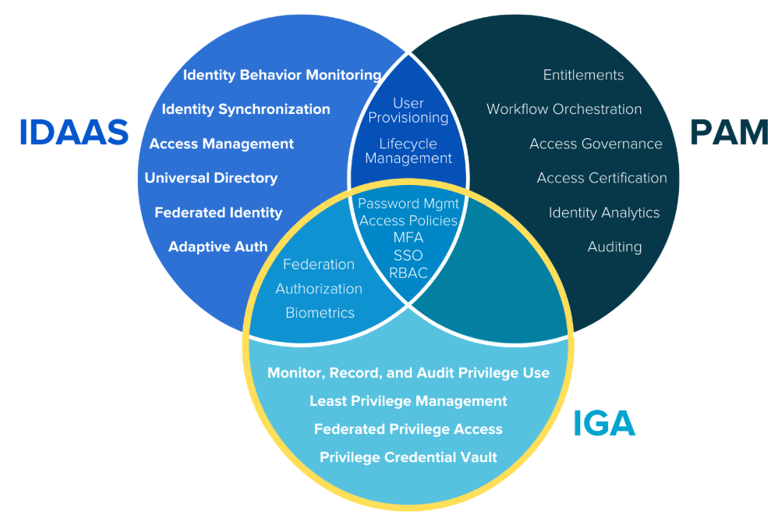
In cybersecurity, IAM, PAM, and IGA are crucial components of identity security.
Here's a breakdown:
IAM (Identity and Access Management):
This is the broad framework for managing digital identities and controlling access to resources.
It involves defining and managing user roles, permissions, and access rights.
Essentially, IAM answers the question: "Who has access to what?"
IAM is the overarching term that the other two fall under.
PAM (Privileged Access Management):
This focuses specifically on managing and controlling access for privileged accounts.
These accounts have elevated permissions (e.g., administrators), making them high-value targets for attackers.
PAM solutions enforce strict controls, such as:
Password vaulting.
Session monitoring.
Least privilege enforcement.
PAM answers the question: "How do we secure access for highly privileged users?"
IGA (Identity Governance and Administration):
This deals with the governance and lifecycle management of user identities and access rights.
It includes:
Automating user provisioning and deprovisioning.
Access certification and reviews.
Ensuring compliance with regulations.
IGA answers the question: "How do we ensure that access is appropriate and compliant?"
In essence:
IAM sets the overall access control strategy.
PAM secures the most sensitive access.
IGA ensures that access is managed and governed effectively.
These three elements work together to create a robust identity security posture.