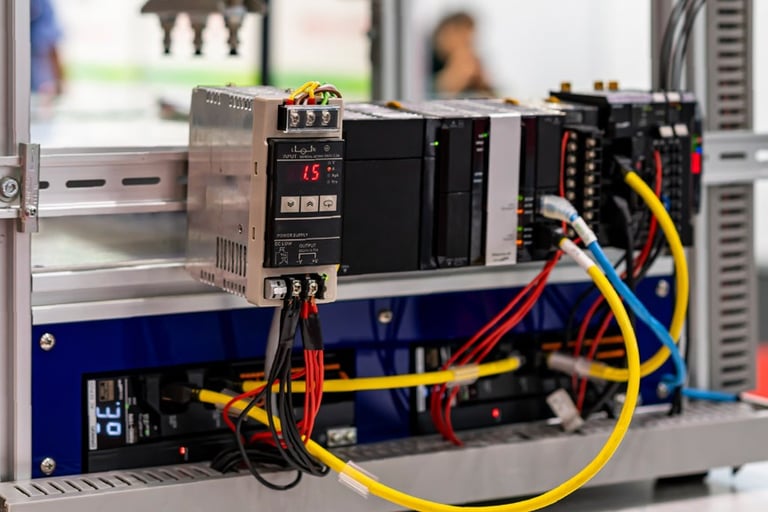
Operational Technologies (OT) and how to protect it from Cyber attacks
Operational Technology (OT) refers to hardware and software that monitors and controls physical devices, processes, and infrastructure. Unlike Information Technology (IT), which focuses on data, OT focuses on the real-world operations of things like:
Industrial Control Systems (ICS):
Including Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and Programmable Logic Controllers (PLCs).
Critical Infrastructure:
Such as power grids, water treatment plants, and transportation systems.
Manufacturing:
Including robotics and automation.
Essentially, OT bridges the digital and physical worlds.
Protecting OT from Cyberattacks:
OT systems are increasingly vulnerable to cyberattacks due to:
Increased connectivity: As OT systems become more connected to IT networks and the internet, they become more exposed.
Legacy systems: Many OT systems are older and were not designed with cybersecurity in mind.
The potential for physical consequences: Cyberattacks on OT systems can have severe real-world consequences, such as power outages or disruptions to manufacturing processes.
Here's how to protect OT from cyberattacks:
Network Segmentation:
Isolate OT networks from IT networks to limit the spread of attacks.
Access Control:
Implement strong authentication and authorization measures to restrict access to OT systems.
Patch Management:
Regularly update OT software and firmware to patch vulnerabilities.
Intrusion Detection and Prevention Systems (IDPS):
Monitor OT network traffic for malicious activity.
Security Monitoring:
Continuously monitor OT systems for anomalies and suspicious behavior.
Backup and Recovery:
Regularly back up OT data and systems to ensure that they can be restored in the event of an attack.
Employee Training:
Educate employees about cybersecurity best practices and the risks of cyberattacks on OT systems.
Risk Assessments:
Perform regular risk assessments to identify and address vulnerabilities.
Zero Trust:
Implement zero trust security models, which operate on the principle of "never trust, always verify."
Incident Response Planning:
Develop and test incident response plans to ensure that you can effectively respond to cyberattacks.
By implementing these measures, organizations can significantly reduce the risk of cyberattacks on their OT systems.