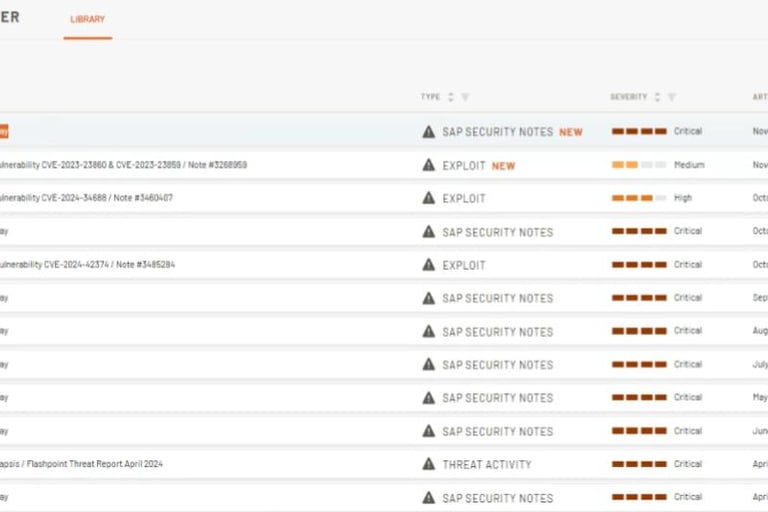
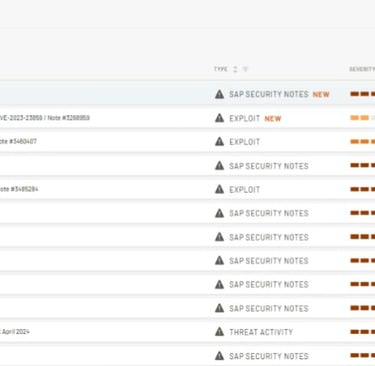
SAP security is a critical aspect of protecting an organization's most valuable data and business processes.
SAP Security:
Comprehensive Protection:
SAP security encompasses the strategies, tools, and processes used to safeguard SAP systems from both internal and external threats.
It's not just about preventing hackers; it's also about controlling user access, ensuring data integrity, and maintaining compliance.
Key Focus Areas:
Access Control:
Managing user authorizations to ensure that individuals only have access to the data and functions they need.
Data Security:
Protecting sensitive data from unauthorized access, modification, or disclosure. This includes encryption, data masking, and other techniques.
Application Security:
Securing the SAP applications themselves from vulnerabilities that could be exploited by attackers.
Infrastructure Security:
Securing the underlying infrastructure that supports SAP systems, including servers, databases, and networks.
Business outcome and goal:
To maintain the confidentiality, integrity, and availability of SAP systems and data.
How to Protect SAP:
Protecting SAP systems requires a layered approach that addresses all aspects of security. Here are some key measures:
Strong Access Controls:
Implement role-based access control (RBAC) to grant users only the necessary privileges.
Enforce strong password policies and multi-factor authentication.
Regularly review and audit user access.
Vulnerability Management:
Keep SAP systems up-to-date with the latest security patches.
Conduct regular vulnerability scans and penetration tests.
Data Encryption:
Encrypt sensitive data at rest and in transit.
Implement data masking to protect sensitive information in non-production environments.
Security Monitoring and Logging:
Implement security information and event management (SIEM) systems to monitor SAP logs for suspicious activity.
Establish audit trails to track user actions.
Segregation of Duties (SoD):
Prevent conflicts of interest by separating critical functions.
Secure System Configuration:
Harden SAP systems by disabling unnecessary services and features.
Follow SAP's security best practices.
Network Security:
Segment SAP networks to isolate them from other networks
Use firewalls and intrusion detection systems to protect against network-based attacks.
Governance, Risk, and Compliance (GRC):
Implement GRC solutions to automate compliance checks and enforce security policies.
Employee Training:
Educate employees about SAP security best practices and the risks of cyberattacks.
By implementing these measures, organizations can significantly reduce the risk of security breaches and protect their valuable SAP data.